INTRO:
Although Klei Entertainment would make the same game twice (as in the case of Shank), the developer has shown willingness to do something different from its previous games. The latter is the case for Invisible Inc.
Invisible Inc. is a turn-based tactics game. It makes use of the reliable system for making moves and taking actions that the XCOM reboots have used. However, instead of awful chance-to-hit rolls and a lot of shooting, Invisible Inc. is about planning and stealthy circumvention of obstacles.
PREMISE:
In the sci-fi dystopian future, corporations rule the world (apparently after a war that shattered sovereign governments). There is extensive practice of cybernetic augmentations, and extensive exploitation too. The corporations seem to be well on their way to turn everyone into a cog in the wealth-making machine.
No corporation could ever stifle human nature though, so eventually there is rebellion. Incidentally, one of the sharpest thorns in the sides of the corporations is an organization that is composed of former corporate agents and operatives. This is the eponymous Invisible Inc., an intelligence agency that has been working for but also against the corporations from its inception.
However, right at the beginning of the story of the game, the corporations have just uncovered its treachery. Its headquarters were raided, and there were few who managed to escape.
The player character is one of those who survived. Specifically, the player character is an “operator”, specifically a mission handler. The player character is tasked with the operation of directing the remaining agents to recover assets and build these up before Invisible Inc. is irrevocably put down. During the process, the player would discover the means through which the corporations tracked down the agency, and a way to land a telling blow on them.
Any player that knows about Neuromancer would recognize the setting for the game immediately. More cynical players might even snicker at it, especially after a few hours into the game; there will be passages that elaborate the latter sentiment later.
TURN-BASED GAMEPLAY:
Most of the gameplay occur in a system that is oriented around turn-taking. There are two sides that are taking turns in a familiarly alternating manner.
One of these sides is the player’s, specifically that of the agents under the player’s direction and Incognita, the AI that Invisible Inc. depends on for computer science work. The other side is the security detail of whatever establishment that the player’s agents are infiltrating; this side is of course CPU-controlled.
The two sides have asymmetric capabilities. The odds appear to be stacked against the player’s side, but the CPU-controlled opposition has the setback of being predictable.

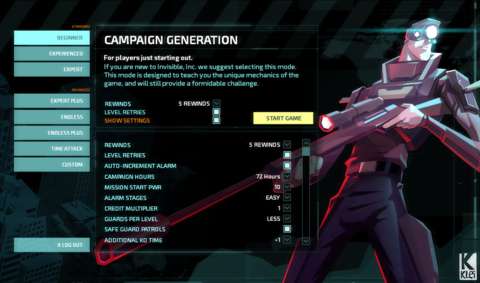
IRON-MAN ROGUE-LITE:
For better or worse, the game does not make it clear to the new player that it is a rogue-lite. The player is expected to complete multiple playthroughs of the game, whether the playthroughs are completed in victory or end in the defeat of Invisible Inc. Every completed playthrough yields “experience points”, which unlock more options for later playthroughs. Furthermore, every playthrough only has one game-save.
This is not unlike what has been done for one of Klei’s previous games, namely Don’t Starve. Like what has been done in that game, this has more than a few problems. For one, each playthrough is considerably long – too long for a run-based formula. Klei had yet to learn from the complaints about Don’t Starve when they made Invisible Inc.
OVERWORLD:
Anyway, the remnants of Invisible Inc. are on the run. They have a rotor-aircraft, but this is a far cry from the well-equipped base that they once had. Furthermore, Incognita, being a powerful A.I. requires more processing power than the aircraft could provide, so it is not functioning at its fullest.
The protagonists have to hit as many targets of opportunity as they can to accumulate resources before eventually coming across the Achilles’ heel of the corporations. However, the rotorcraft cannot be everywhere at once.
That said, the overworld shows the location of the rotorcraft and the locations of potential targets. The player picks the target for the next mission.
The relative distance between the rotorcraft and the target will be a factor though. Longer distances require more time to travel across, so the player will want to measure the time taken against the rewards that can be had from the target.
The overworld is also where story developments occur. The player is also shown conversations between the characters that are voiced. Most of these can seem under-presented though, especially if one considers Klei’s pedigree in making animated cutscenes.
PASSAGE OF TIME TO ENDGAME:
A timer shows the amount of time remaining before Incognita becomes irrevocably degraded. Travelling time subtracts from the timer. Doing things like managing finances and improving agents also causes the timer to tick down, albeit in term of seconds according to the number of real seconds that the player uses to make those decisions.
The time that passes during missions does not subtract much from the timer, however. This can seem at odds with the emphasis on there being limited time, but there is another source of urgency during missions that will be described later.
Running out of time does not really end the playthrough in failure though. Incidentally, as the player performs and complete missions, the corporations ramped up their coordination to increase security at their sites. Gameplay-wise, this increases the challenge from subsequent missions, but narrative-wise, this allowed Invisible Inc. to triangulate where their centre of coordination is. When the timer reaches zero, the protagonists will find this centre, and their final mission is to infiltrate it and subvert its automated system to the will of Incognita.
In the meantime, the player takes on missions that would reward the remnants of Invisible Inc. with the resources to prepare for the all-or-nothing mission.
MISSIONS:
These missions are represented on the overworld as icons; selecting them brings up a screen which shows pertinent information about these missions. The most important pieces of information are the objectives, the guaranteed rewards (though the exact rewards are unclear) and the general composition of enemies.
The information also includes the time that the aforementioned rotorcraft needs to travel to the mission location. This is important in the long run, because longer travel times means fewer missions and thus fewer opportunities to gather the means for prevailing in the final mission.
PROCEDURALLY GENERATED MISSION AREAS:
Ultimately though, the information from the mission briefings is still patchy and certainly not enough for the player to prepare builds that are specific yet effective for any upcoming mission. The player is better off going for versatile builds.
This is because each mission area is procedurally generated; despite the prevalence of the corporations, they never standardized the layouts of their properties. Therefore, the player’s experience throughout the playthrough may vary greatly.
For example, one mission may have the agents starting on one end of the level, and the exit is on the other end of a relatively linear stretch of rooms. For another example, the exit for the level could be in a room adjacent to the room where the agents started in.
That said, the computer-controlled security detail at the mission areas always know the layouts,
SQUARE TILES:
All levels have layouts that are practically grids of squares. A square may be occupied by an active character, an interactive object or an obstacle, but never a combination of these. As for inactive characters, there can be two knocked-out NPCs on a square, i.e. one lying on the ground, and one that is being dragged around by an agent.
The edges of the squares may have walls set along them; walls are typically used to separate clusters of squares into rooms. Instead of a wall section, there may be doors too.
AGAINST THE ODDS:
Even though the CPU-controlled opposition are not particularly bright (laughably so at the lowest difficulty settings), the corporation still has considerable advantages over the protagonists. These advantages include unending reinforcements, all of whom are armed with guns that the player characters cannot use.
Furthermore, the mission locations are in facilities that can only be reached with sci-fi teleporters, which can detect unregistered guns. This means that the player’s agents cannot use loud and forceful entries into the mission areas, at least not without inciting overwhelming responses.
Using teleportation to insert agents into the mission areas also immediately trigger their automated security systems. Although the alarm is not raised immediately, the systems do detect signs of intrusion and will raise its response over time. This is the narrative excuse for a gameplay element that will be described later.
As for the player’s agents, they initially do not have a lot of equipment that can get past the corporate scanners in the mission areas. They have to make do with black market devices, which do not have enough capacity for anything other than short-duration missions. The security detail does not have such concerns; they never run out of ammunition or energy for their own equipment.
THE OPERATIVES - OVERVIEW:
The player’s operatives – also called “agents” – are the player’s main assets. They are the ones risking their lives to execute the missions and retrieve whatever that is required from the missions.
The operatives are augmented in one way or another, but they are ultimately still human. Any corporate goon or drone that fires on them would knock them out outright. Therefore, the player will not want them to get them into trouble that they cannot get out of unharmed; downed agents are liabilities.
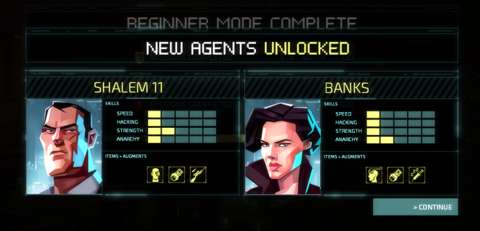
The player begins with only two operatives; new players get two specific ones. Subsequent playthroughs allow the player to select the starting agents. Eventually, the player would come across at least two other agents to fill in the two remaining agent slots, thus gaining a full team of four. The player will need each one, mainly to cover more ground within an amount of time, or so that they can support each other.
Being still human, they can only carry so many things on their person. This is despite the presence of definitely sci-fi tech, such as teleporters. That said, the player will want them to carry as many items as possible, because these are the means through which agents can deal with obstacles in their way. Furthermore, there are missions in which they must retrieve things from the mission area, and these things take up space in their inventories.
Therefore, the player has to manage their inventories carefully. Indeed, such gameplay is not for players who consider mucking around with icons and slots to be a tedious affair.
AGENT STATS:
Any agent has four statistics: Speed, Strength, Hacking and Anarchy. These determine their other statistics and the items that they can use, so the player will want to invest in these in the long-term so that the agents become effective members of the team.
Oddly though, these statistics are improved by spending money on them; higher levels require more money, of course. That said, the narrative of the game is unclear on how they can be improved in a short time and aboard a rotorcraft. (There are mentions of “programming” techniques, e.g. mental conditioning, but if this is the case, this is really a sci-fi excuse that is as unbelievable as the use of teleporters and convenient nanotech.)
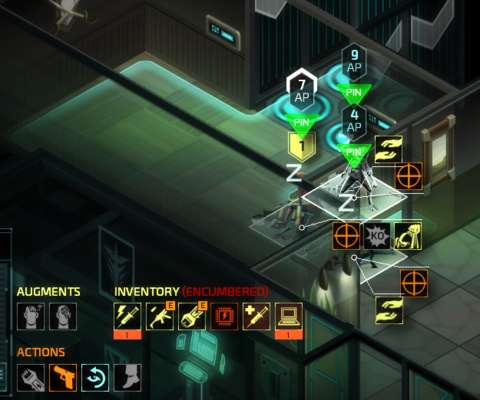
ACTION POINTS & MOVEMENT:
The agents’ ability at moving about is perhaps the most important aspect of their performance. Being able to move far and often makes an agent more versatile.
An agent’s ability to move is determined by his/her Action Points. Every tile in a cardinal direction costs 1 AP to move across. A tile in a diagonal direction has a trickier cost that is unfortunately not made clear to the player. The first of such tiles in any turn requires two points. However, the second diagonal tile requires only one point, whereas the third requires two, and so on, alternatingly.
The player is shown how many APs remain after an agent moves anywhere, though the agent and destination tile have to be within the same screen.
The player is also shown the path of the agent. If the path would move onto a revealed zone that is under observation by any security detail, the lines of the path will also be coloured. Red means that the agent will be discovered, whereas yellow means that agent’s passing would rouse suspicion in the observer, who will then go over to the pertinent tile to check things out.
The player is not shown the amount of movement that enemies have, but there is a feature to predict their expected paths. This will be described later.
SNEAKING AND SPRINTING:
By default, the agents sneak about, keeping as quiet as possible; the player can hear them tip-toeing about, though enemies cannot hear them.
If the player has not have them spend any APs to sneak about, the player can have agents sprint about instead. Sprinting gives them additional APs for movement and any other action that requires Action Points. However, the agent makes a lot of noise, which can be heard by enemies that have hearing.
The player can have agents toggle back and forth between sneaking and sprinting as long as they have not spent APs on moving. After spending any APs, the agents are committed to that movement mode.
ATTACKS:
The agents can make attacks; attacks do not spend Action Points, but instead uses their own resource. To elaborate, each agent can make one attack in his/her turn. Certain circumstances can let him/her make more, but generally one attack is all he/she gets, regardless of how many weapons that he/she has.
As for the attacks, they can be made using either lethal or non-lethal means. Deciding which to use is important, because either type has its own setbacks. That said, a permanent end to enemies is not always a good thing, as will be elaborated later.
On the easier difficulty settings, there are generally a small number of enemies such that the limitation of just one attack per turn is not of much concern. However, at the higher difficulty settings, there are often more enemies than the agents could deal with, so the player will want to consider distracting or bypassing them instead, if possible.
PINNING & DRAGGING:
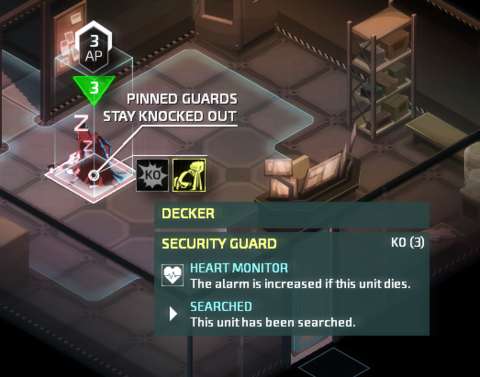
An agent can apply pressure on the vital points of a human enemy that has been knocked out; the agent does this automatically when he/she is on a tile with that downed human enemy and there is nothing else that he/she can do. This prevents downed enemies from waking up, i.e. freezing the timer that counts down to when they wake up.
A downed human enemy can also be dragged about, typically to shift his body about. This is so that he is not seen by other security detail, which immediately become alarmed if they do. Dragging him elsewhere also determines which room that he will search first; there will be more on the searching patterns of enemies later. (By the way, the security detail, where they happen to be human, all appear to be men – sometimes with the same face shape.)
An agent that is pinning or dragging a human enemy that has been knocked out cannot do much of anything else. He/She cannot open doors when dragging someone.
OVERWATCH:
Invisible Inc. has its own overwatch system, e.g. a way to have agents shoot at enemies that enter their view. However, ranged weapons are exceedingly rare.
Armed enemies, by default, go into overwatch when they spot the player’s agents. This works slightly differently from the overwatch that the player’s agents can do. There will be more elaboration on this later.
AMBUSHING:
Invisible Inc. has a melee-oriented variant of overwatch. This makes agents attack any enemy that comes within one tile of them along the cardinal directions. Obviously, as the name of this action would imply, the player will want to place agents around corners or doors to avoid being spotted.
PEEKING:
The procedural generation of levels can make scouting a difficult endeavour that could be further compounded with fickle luck. Fortunately, Klei has thought of this, and has implemented the gameplay element of “peeking”.
When an agent is at a corner that leads into somewhere else, the agent can spend one AP to look around the corner. This reveals anything in view that is within 90 degrees around that corner in either direction. Sometimes, more is revealed if the room happens to be spacious.
An agent can also peek around open doorways. If the agent happens to be right in front of a doorway, he/she can have a 180-degree view of the next room. If the agent happens to be next to the doorway, the arc is narrower, but of course there is less risk of the agent being seen.
Peeking will never tip off enemies, no matter how alert they are. Therefore, peeking would be an important method of reconnaissance.
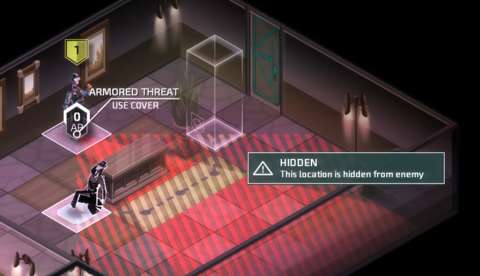
HIDING:
When an agent is next to a piece of cover or next to a doorway, the agent automatically goes into a lurking posture, depending on what he/she is using to hide behind. Any enemy that is directly on the other side of the cover will not be able to see them. Enemies that are in a direction that is oblique to the piece of cover might be able to see them, but the oblique angle has to be less than 45 degrees for this to happen.
Low pieces of cover, such as furniture, will not block the line of sight of agents. This is an advantage that the player should do well to exploit, though such pieces of cover are not any more common than the higher ones.
FOG OF WAR:
Since the player’s side is the intruder, the player does not get to see what the player’s agents cannot see. Fortunately, hacked cameras will show whatever that they are looking at to the player, and will continue to do so until they reboot.
Interestingly, the fog-of-war system is only updated at the end of the player’s turn. To elaborate, anything that the player has seen during his/her turn remains revealed, even if his/her agents have moved away. This is very convenient, especially if the player is planning actions in tandem.
THE QUICK AND THE DEAD:
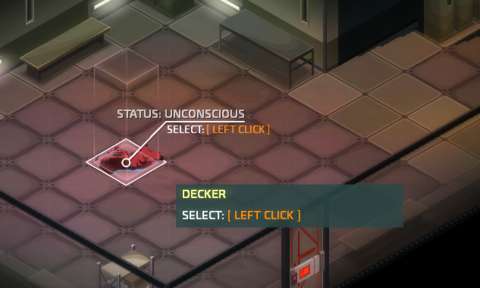
There are no life or health meters whatsoever. Characters are alive, dying, unconscious or dead; the latter three states, especially the final one, render characters non-functional. There is nothing in between these states.
The agents are tough, but only enough to survive the gunfire that put them down on the ground. They are dying, and will eventually be permanently dead if the player does not have them revived. That said, only other agents can revive them, and they have to do so through the use of medical kits. Otherwise, the only way to retain their service is to have other agents drag their unconscious bodies over to the exit teleporters and leaving. This tends to lead to a sub-optimal outcome.
GEAR & AUGMENTATIONS:
On their own, there is not much that they can do. They do not even have martial arts moves, even though characters like Nika has been described as being physically capable of these. Rather, what they can do is determined by their gear and augmentations. However, these have to be stolen from the corporations, or bought from Invisible Inc.’s black market contact.
In the case of gear, their aforementioned statistics determine the variety of gear that they can use. Typically, higher statistics are needed for higher gear ratings. Augmentations have less restrictions, but there are fewer slots for augmentations than there are slots for gear. Furthermore, augmentations are installed permanently; they cannot be removed or changed.
Speaking of slots, agents start with only a few of these. Gear slots can be increased via increases to an agent’s strength. An agent can eventually have quite a number of gear pieces, thus giving him/her considerable versatility.
Slots for augmentations are not readily obtained. Instead, they have to be gained from cybernetics facilities. These facilities have machines that can install particularly rare augmentations, or make available more slots. The latter is not a delicate process; it will temporarily knock out any agents that undergo it. Furthermore, machines that perform the process are often guarded by particularly nasty enemies.
As for the variety of gear and augmentations, they are considerably many. This design is intentional, because it allows for the development of agents with wildly varying capabilities. However, this also means that any unique capability that an agent has at the start of a playthrough would eventually have its usefulness diluted.
TRICKING OUT AGENTS:
The agents are always outnumbered and outgunned, so their versatility and quality are the main means through which they can deal with the opposition.
However, there can only be so many opportunities to develop their capabilities and resources. Therefore, early in the playthrough, it is in the player’s interest to specialize specific agents for something so that team members can complement each other. For example, having an agent augmented and improved for melee attacks makes that agent useful for keeping enemies down for a long time.
Of course, developing agents to have greater versatility would be a wise decision too. There are only ever four team members, so having any one of them able to do anything that the others can do would be convenient.
Certain types of gear and augmentations will be mentioned later, due to their significance in the gameplay.
UNIQUE AUGMENTS:
Each named agent comes with his/her own augment. Some are highly situational; for example, there is Nika’s augment, which grants her APs when she knocks out (or kills) enemies. Of course, that means messing around with enemies, which is usually not a good idea.
Some other unique augments practically must be had. For example, Internationale’s augment reveals the presence of nearby mainframe devices (more on these later) and allow the remote hacking of computing terminals within the same range. This can happen even if the agents had not seen them with their own eyes. This makes her near-indispensable to almost any playthrough.
NEURAL DISRUPTORS:
Neural disruptors are practically futuristic tasers, with particular intended use against augmented humans. These are the most common non-lethal melee weapons. Indeed, these are the only melee weapons around. The player should not expect agents to be carrying around knives and other lethal implements, and as mentioned earlier, they will not use martial arts to knock out enemies.
Neural disruptors knock out enemies for a few turns. They need to recharge afterwards, during which the agent cannot use the neural disruptor. This means that the density of enemies is a factor to consider, if the player intends to clear the way to the objective by knocking out the opposition.
FIREARMS:
Firearms remain the main means of dealing lethal harm in the sci-fi dystopian future. Almost all enemies, except camera drones, have these, either in their arms (in the case of the humans) or on their weapon mounts (in the case of drones).
Firearms can never be removed from enemies. This is understandable in the case of the drones, because their guns were not made for human hands. In the case of the guns of human enemies, they are described as having been gene-coded to their users.
Such limitations are understandable, if only to deny the player easy access to guns. What is less understandable is the omission of any means of sabotaging the guns of knocked-out enemies.
Anyway, guns are generally only found in the possession of enemies. The player’s agents can have guns too, but according to the narrative, there are not many guns that can get through the teleportation process without triggering alarms.
That said, gameplay-wise, the benefit of range from firearms is balanced with the setback of limited shots. Some firearms can only be fired so many times before they run out charges permanently. There will be more elaboration on charges later.
Some guns can be loud; typically, these are the lethal ones, unless they happen to have noise suppression. Non-lethal guns are less noisy; indeed, one of the less-lethal handguns make no next to no noise.

CHARGE PACKS:
Many devices in this game’s sci-fi future have internal energy sources, or even nano-forges that reload them with freshly produced materials. Even the firearms use such tech, what with bullets having long been phased out.
Thus, there are charge packs, which are consumable items. Where most other pieces of gear are reusable (and thus have cooldown timers), charge packs are immediately consumed when they are used.
This is just as well, because their main effect is to immediately end the cooldown timers on other items that have been recently used. They can also refill the magazines/reservoirs of guns with limited ammunition. Both have to be done during missions, including the latter case (even though the latter case could ostensibly be done in between missions).
PARALYZERS:
Knocked-out human enemies can have their knocked-out durations refreshed by re-applying knock-out solutions on them, but the durations are merely reset according to the capabilities of the player character, not added. However, Paralyzers increase the number of turns during which a human enemy is knocked out.
STIMS:
Stimulants give a number of bonus APs to the agent for use in his/her turn. The stims can be used at any time during the agent’s turn, which is convenient.
“ANARCHY” ITEMS:
Anarchy is an agent’s skill at stealing things from human enemies. For whatever reason, having higher Anarchy skills means that more money can be stolen.
The other reason to have significant Anarchy levels is the enabling of the use of Anarchy items. Anarchy items could have been parked under the ‘hacking’ category of items, but they have been placed under Anarchy likely for purposes of gameplay balance.

COOLDOWNS RETAINED IN ITEM TRANSFERS:
Typically, pieces of gear have cooldowns in order to balance the advantages/benefits that they provide. The cooldowns are measured in turns.
Interestingly, item cooldowns are retained whenever items are transferred around. Cooldowns stay with items that have been dropped onto the ground, and they stay when they are exchanged between agents.
One of the things that the meticulous player would do is to have agents pass by each other when going somewhere else, if only to exchange items that are under cooldowns.
MISSION-SPECIFIC ITEMS:
Some missions require the retrieval of an item, or getting some item to something within the mission area. These items do nothing useful, so one of the player’s agents has to use a gear slot to carry these around.
In the case of objectives about retrieval of items, there is a further complication. The rooms where these items are located are often far from the exit rooms, in terms of movement distance. The agents may also have collected other things along the way, so some inventory management would be needed.
KEYCARDS:
Some enemies carry keycards. These are the only means to unlock locked doors. The keycards can open the locked doors, permanently; they cannot be re-locked, which is perhaps a lost opportunity.
Enemies that do not carry the necessary cards cannot open the locked doors, much less move through them. Therefore, the player will want to carefully consider which doors to unlock, because this will give enemies greater freedom of movement too.
MAINFRAME VIEW & HACKING:
Incognita is always with the infiltration team, monitoring their progress and hacking anything that the player directs it to. As mentioned earlier, Incognita has inserted itself into the mission area’s system. Although it cannot be purged in any way, the local system knows that something is wrong. This is the excuse for the implementation of the alarm level, which will be described later.
Anyway, Incognita can hack into any system that the agents discover. The reason for the need to have agents discover them is not entirely clear; it is likely a deliberate gameplay limitation.
That said, whatever system devices the agents have discovered is what Incognita can monitor. Whatever it monitors can be seen in the “Mainframe view”. This shows the wireframe layout of the level, and the devices that are connected to the security system of the mission area. Any devices that have been discovered, including any that is dormant, stay in the Mainframe view permanently.
FIREWALLS:
None of the devices that are connected to the mainframe of the local system are defenceless. They have firewalls, which are implemented as ablative hit-points. These firewalls have to be broken down before the devices can be taken over.
Generally, the firewalls would be on trips to zero, but there are some nasty responses by the local system’s Daemon programs (more on this later) that can restore them, or otherwise raise them across the board.
The devices that are yet to be powered, such as cameras that are yet to come online, cannot be hacked, for obvious reasons. Machines that are rebooting after having purged a hack cannot be hacked either, at least until after they have fully rebooted.

“PWR”:
Incognita cannot simply compromise any device outright. Rather, it needs to divert processing power from the local system to do so, and that power is lost to it afterwards (presumably because the local system recognizes it as having been compromised and quarantines it).
Gameplay-wise, this is the narrative excuse for the implementation of the “PWR” resource. This resource is obtained by having agents physically compromise computing terminals; it is not entirely clear why Incognita cannot do this itself. That said, the agent’s Hacking skill determines how much “PWR” that Incognita gets.
“PWR” can also be gained through other means, usually through Incognita’s own programs; these will be described later.
By default, Incognita can only store up to 20 points of “PWR”. Any more is wasted. Therefore, the player will want to spend any surplus “PWR” where possible, though the presence of Daemons can make this difficult (more on Daemons later).
PROGRAMS:
Although Incognita is actually a powerful AI, the remnants of Invisible Inc. only managed to save its core programming, and the rotorcraft lacks the processing power to enable its full functionality. This is the narrative excuse for Incognita having only up to five programs.
In the first playthrough, it starts with the “PWR Drip” program, which gives one point of “PWR” every turn. It also has a program that can remove one level of Firewall in return for spending two points of “PWR”.
Most programs require “PWR” to be used, though some like “PWR Drip” gives “PWR” instead. The player will want as many programs as possible so that there are many options for hacking the local system. However, as mentioned earlier, there is a limit to the number of programs, and sources of programs are not easy to come by.
Speaking of which, Invisible Inc.’s black market contact may offer these programs sometimes, but the main source of these programs are the compromised software kiosks in the mission areas. Somehow, third-party hackers have set up shop in these kiosks, running vendor-bots that sell programs to the player.
DAEMONS:
The firewalls are not the only defences that the local system has. Some devices are loaded with Daemon programs. Which devices have these are revealed when the devices are found, but the type of Daemon is not shown. Some are worse than the others, so the player is taking considerable risks when hacking devices with unknown Daemons.
These programs trigger whenever the Firewalls of their devices are completely broken down. They are expended, but not before effecting their functions. Most of these are bad for the player. For example, there is a Daemon that increases the Firewalls of all devices by one level.
The Daemons that appear later in the playthrough and/or at higher difficulty settings are substantially nastier. Some are practically upgraded versions of earlier-encountered Daemons.

REVERSE-ENGINEERING:
Incognita would not just let every triggered Daemon perform its function. There is a small chance that the AI can capture the Daemon and reverse–engineer it for greater access to the local system. This greater access comes in the form of buffs for either Incognita’s programs or for the agents’ own capabilities.
The buffs are randomly selected from a small number of possible buffs; the type of Daemon that is reverse-engineered does not matter. The buffs are usually useful, such as one which reduces the amount of “PWR” needed to perform hacking.
ENEMY BEHAVIORS – OVERVIEW:
Obviously, the security detail at any mission area do not take kindly to intruders. Also, being part of their jobs or functions, they will patrol the mission areas or stand sentry at locations that are strategic, e.g. corners where they cannot be snuck up to from behind.
The difficulty settings for playthroughs include options that determine the complexity of the behaviours of the enemies. The settings also include what the player’s agents can do to these enemies and disincentives for messing with them. There will be more elaboration on these gameplay elements later.
The behavioural elements that are generally not affected by difficulty settings will be described first.
DISTRACTED ENEMIES:
If the player’s agents make noise that are heard by human enemies, these enemies would come over to investigate the location of where the noise occurred. If noises are not particularly alarming, e.g. loud footsteps, the enemies eventually revert to their routine patrols if they did not notice anything else out of the ordinary.
However, if the noises are gunshots or something just as alarming, they are alerted indefinitely. Alarming noises also raises the security alert level.
If the player’s agents have opened doors, these doors will be tagged with a hidden marker that indicates that they have been opened by characters other than those on the security detail. If enemies on patrol notice these, they will be distracted by the open doors and will move over to investigate them and the room beyond. This happens to be a reliable way to get enemies away from their patrol routines.
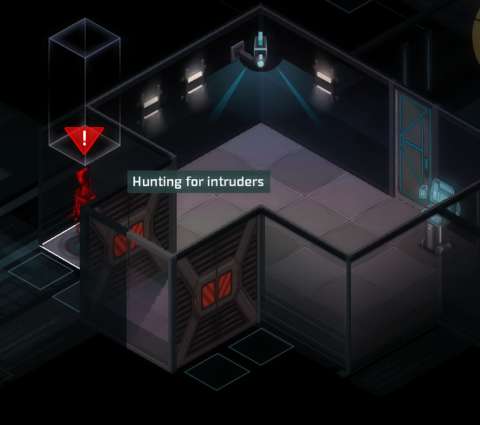
ENEMIES WAKING UP & SEARCHING:
Human enemies that woke up after being knocked out and drones that rebooted after being hacked immediately become aware that they have been assaulted. They will begin searching the level, starting with the room that they are in, and will stay in this state indefinitely.
Therefore, it is in the player’s interest to try to avoid assaulting enemies in the first place, if possible. If the player has to, it is best to vacate the rooms that they are in and the adjacent rooms as soon as possible, in order to avoid their search routines.
That said, these enemies will search the rooms that they woke up in. Therefore, it might be wise to drag them into rooms that are further away from rooms that have the objectives or the exit teleporters.
Enemies that are searching about will analyse the rooms that they are in, thus noticing any blind spots. They will spend their next turn checking these out. In other words, if the player has an agent or an asset inside the room and they stayed put, they will eventually be discovered. However, if an agent has a lot of APs, he/she can stay ahead of the search.
AGENTS SPOTTED BY CAMERAS AND DRONES:
If the player’s agents are spotted by cameras or camera drones, the alert level is immediately incremented. Nearby combat-capable enemies will be alerted to the last-seen locations of the spotted agents. In the case of camera drones, they chase after the player’s agents and will continue reissuing alerts to nearby enemies whenever they catch up and see the agents again.
Enemies that are alerted in this way stay alerted indefinitely. Therefore, the player will want to keep an eye out for cameras and camera drones when going into the next room. In particular, cameras that have yet to be powered on will remain hidden, unless revealed through special means.
SOUND DETECTORS:
Mission areas of great importance tend to have sound detectors. These can detect loud noises, like those emitted by sprinting and guns that are not suppressed. Sound detectors that are tripped will immediately raise the alarm level (more on this later).
ENEMIES ACCOSTING AGENTS:
In most missions, the security detail are not on orders to terminate any intruder on sight. Indeed, if they come across any intruders, they will accost them first. They also set up “overwatch” fields, which would be familiar to any players that are experienced with turn-based tactical games. The agent – or agents – that they have accosted will not trigger shots from these enemies, as long as they stay in place. However, any other agents that stray into the field will get shot.
Enemies that have set up overwatch fields will also alert other nearby enemies, but will otherwise continue the overwatch and stay where they are. This makes them vulnerable to any agents that are approaching them from their blind spots.
If the agents that are being accosted move onto tiles that enemies on overwatch can see, they will be shot at. However, if the agents move onto tiles that they cannot see, the overwatch is broken. If the agents move behind cover that they can see, they will shoot, but hit the cover. This makes a lot of noise, however, and will alert other enemies in hearing range.
If an enemy that is on overwatch fails to hit an accosted agent, the enemy will reposition itself to get a clearer shot. If its overwatch is broken, the enemy attempts to investigate the last-known location of the agent. In either case, if the enemy spots the agent (or another one), it accosts the latter and sets up another overwatch field.
Understandably, enemies that have accosted agents will be alerted indefinitely.

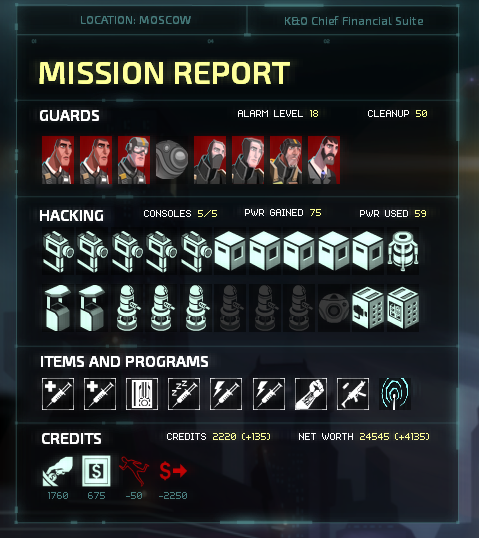
ALARM LEVEL:
All corporate facilities have to be accessed via teleportation; this makes infiltration a tad complicated, because coming in Terminator-style is not subtle. In this matter, Incognita provides Invisible Inc. with an indispensable service: she can hack into the mission area’s system to allow agents to come in at inconspicuous locations. This is not a perfect science though; its intrusion still triggers the more paranoid sub-routines of the local security system.
This is the narrative excuse for the implementation of the alarm level. The alarm level introduces progressively nastier complications as it increases.
The tracker for the alarm level is partitioned into a radial meter with several segments. The number of segments is determined by the nominal difficulty rating of the mission; higher ratings mean fewer segments.
By default, the tracker for the alarm level automatically advances by one segment every turn. This automatic advance can be disabled, but this greatly reduces the urgency of missions.
Whenever the player inadvertently or deliberately trips alarm sensors, the tracker advances. Alerting enemies and having the presence of agents confirmed also advances the tracker.
When the meter has all of its segments filled, the alarm level increases by one. When this happens, a complication is introduced. Higher levels generally deliver worse complications.
COMPLICATIONS:
The first complication is usually the activation of more cameras, if they have not been activated already. Certain characters can discover these inactive cameras, so the player can be forewarned. If these persons are not around, the player is still given one turn before the devices boot up.
More severe complications include the installation of more Daemon programs, or the arrival of more guards. Some can even hobble the player’s agents indefinitely for the duration of the mission.
HEARTBEAT & CONSCIOUSNESS MONITORS:
Stealth-oriented games that are not carefully designed often indubitably let the player character eliminate enemies willy-nilly. Besides, there had never been CPU-controlled enemies that are scripted to be smart enough to deal with stealthy player characters.
Therefore, Klei’s developers have implemented disincentives for eliminating enemies outright, in addition to making it hard to kill them in the first place. (There are no means to kill enemies that have been rendered unconscious, by the way.)
Firstly, all human enemies have heartbeat monitors; this is a given. If any human enemy is killed, the alarm level increases.
Secondly, there are enemies that do have consciousness monitors. Knocking them out raises the alarm level too. At higher difficulty settings, all enemies can have consciousness monitors.
DRONES:
Drones are, of course, non-living things. They do not have consciousness or heartbeat monitors, so they can be eliminated without raising the alarm, if the player can do so quietly. However, since they are not living things, they are immune to neural disruptors and toxin-based attacks. They can only be destroyed, and usually through loud means. Therefore, eliminating drones is usually a fool’s errand. However, if the player could knock them out, “PWR” can be harvested once from their remains.
Drones behave a lot like their human counterparts. The main difference is how they detect intruders. For whatever reason, the drones do not have audio receptors, so agents can sprint past them without them noticing. However, the drones always end their turns by using their short-range scanners, which will detect any intruders in range, including those behind opaque obstacles.
(In the case of agents behind obstacles being detected, the drones are not immediately alerted, but they will be looking at the direction of the obstacle.)
TAKING OVER DRONES:
Drones can be hacked, because they are connected to the mainframe. Hacked drones come under the player’s control, and can be directed around like an agent. However, enemies that can detect the compromised drones will know that they have been compromised, and will respond to the drones like they would the player’s agents.
REBOOTING DRONES:
Generally, hacked drones can only be controlled for one turn. In the next turn, their electronic defences cause them to shut down and reboot, which restores their firewalls. Thus, the player should not expect to be able to turn the enemy’s drone assets against them for long.
ARMOUR:
Some enemies have armour. This serves as immunity to attacks that do not have Armour Piercing properties. However, they do not do anything against incoming attacks that do happen to penetrate armour.
Usually, an enemy’s armour rating is intrinsic, i.e. it cannot be changed. However, there are some enemies that have armour that is complex enough to have specific weaknesses. For example, certain OmniTech guards have armour that can be eroded by reducing their firewalls.
CHANGES IN ENEMIES AS PLAYTHROUGH PROGRESSES:
At the default playthrough settings, the enemies that the player would encounter in the early days are push-overs. The enemies that appear later in the playthrough are better protected. Their betters also happen to have better gear, such as consciousness monitors and stronger armour.
However, the lesser ones are still around. At the default settings, these are still more numerous than their betters.
DIFFICULTY SETTINGS FOR COMPOSITION AND COMPLEXITY OF ENEMIES:
Generally, as the playthrough progresses, the player would face more enemies that are more troublesome than the earlier-encountered ones. If the player wishes to have more challenge from the game, there are difficulty options that have these troublesome enemies appear earlier, outnumber the lesser ones or even replace them entirely.
Indeed, there are many difficulty settings that are available to the player in the build of the game at this time of writing. The player can have settings that make a playthrough dauntingly difficult, e.g. having many guards with long patrol paths that go from room to room, and a paucity of resources for the player’s agents to use.

MONEY:
In this game’s dystopian sci-fi future, the use of money has become so incredibly pervasive that having money around is always handy. Thanks to the presence of nanotechnology, vending machines are now practically miniaturized factories that can produce many things.
In the mission areas, the “nano-fabricators” – as the vending machines are known as – initially prevent the player’s agents from using them. After they have been taken over, they cannot just crank out items immediately; presumably, this will immediately raise the alarm.
Thus, there is a money account that the player’s agents have access to, even during missions. It receives any money stolen from the corporations and its henchmen. The money is then used by agents to make purchases from any vending machines and kiosks that have been compromised. Having agents do some shopping while undertaking covert missions can seem odd.
Perhaps more believably, money can be spent on making purchases from Invisible Inc.’s black market contact. He has a much smaller variety of offerings, mainly due to him spending most of his time and effort to track down the centre of the corporations’ network. However, he does purchase surplus or unwanted items –a service that the aforementioned machines cannot provide so readily. However, due to the limited space on the rotorcraft, the player can only store up to five items in it; anything else has to be carried around by the agents.
VISUAL DESIGNS:
The narrative mentions that augmentations are common among the people of the dystopian sci-fi future, especially if they were/are corporate employees. However, if the player is expecting augmentations as obvious as cyber-limbs or protrusions from one’s head, the player would be disappointed. Thanks to the convenient excuse of nanotechnology, most of the augmentations are discrete or flush with human skin.
The most obvious augmentations are the ear-muff-like devices that some characters sport, but even so, it is unclear whether these are just headwear or augmentations.
The same complaint about inadequately sci-fi visual designs for sci-fi things can also be directed at the guns that the humans use. The guns have been described as having rather exotic technology, like a tiny nuclear reactor in the case of the Flurry Gun. However, they have models that have the silhouettes of real-world guns. There is, of course, the excuse that nanotechnology made this visual familiarity possible, but this excuse is old.
In contrast, the guns on the drones certainly look sci-fi, especially those on the bigger drones. Speaking of which, the drones look very much sci-fi, most of them either being floating spheres or insectoid in appearance.
Perhaps the least impressive visual designs are those for the level environments, especially considering the artwork that Klei has done for the environs in its other games. This is not because they are drab; they are quite detailed and varied.
The problem is instead the black backdrop. The backdrop has wireframe copies of the rooms floating around, but little else. Due to this aesthetic design, there is no immediately noticeable indication of where these mission areas are in the sci-fi world of the game.
SOUND DESIGNS:
Music is the best aspect of Invisible Inc.’s sound designs, and it so happens to start itself with this. Many of the tracks provide an appropriate sense of urgency. Despite the turn-based nature of the gameplay, the game does have coding that assesses the current situation and changes tracks accordingly. For example, as the alarm level increases to untenable levels, the music switches to more ominous tracks.
Voice-overs have rarely been on Klei’s list of priorities. This is especially noticeable in Invisible Inc., more so than its other games. This is not for the better.
There are only three characters that have legible voice-overs: the founder of the agency, the agency’s most reliable black market contact and Incognita. The voice-overs for the first two characters are satisfactorily delivered; they do give the impression that they are grizzled veterans of spy-craft. Incognita sometimes slips into inane statements, which gives impressions of GlaDOS from Portal, for better or worse.
Unfortunately, this paucity of voiced lines particularly highlighted the absence of any voice-overs for the other characters, especially the agents. Considering that there are only a handful of agents, they could have benefited from sophisticated expressions of their character. Rather, the most that they would get are dialogue boxes that appear near the upper corners of the screen during the start of the missions.
At least the illegible utterances of human characters have voice-overs, which provides decent satisfaction of having done things like knocking out human guards.
Most sound effects are associated with gameplay occurrences, so the player will want to keep an ear open for them and learn which sound is which. Nevertheless, the camera will automatically pan to show the player what is happening, if they are within the line of sight of any of the player’s agents or compromised cameras.
SUMMARY:
Invisible Inc. is not a simplistic game, and it is noticeably different from many other turn-based tactical games. The onus is on keeping a low profile as much as possible. There are no annoying chance-to-hit rolls because gunfights are not a core element of the gameplay.
In other words, like Klei’s previous games, Invisible Inc. fulfils the design goal of being a game that is different from others of its ilk. There is enough similarity, such as the turn-based gameplay and point-based movement, such that veterans of turn-based tactical games would find the game to be familiar. Yet, there is enough innovation to make it stand out from the rest, such as the disincentives against elimination of enemies.
Unfortunately, Invisible Inc.’s most notable flaws also happen to be shortfalls in what Klei is expected of. The game’s presentation is perhaps the least convincing and impressive among Klei’s products. The sci-fi dystopian setting of the game relies on outlandishly fictitious technology like ground-up nanotech and teleportation, which are often used in video games for hand-waving explanations.
Overall, Invisible Inc. would give the impression that it has competently designed gameplay – but it is far less memorable than the other games that Klei has made.