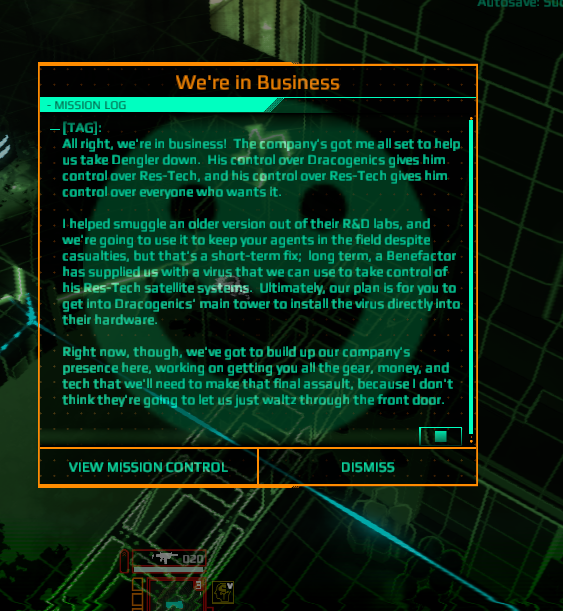
INTRO:
The first Syndicate was a seminal game. It showed that a darkly fun game can be had from the otherwise grim and dystopian setting that is cyberpunk.
(It also propelled Peter Molyneux to fame, for better or worse. That said, people who have worked on the first Syndicate had given him credit for some of the game’s best ideas.)
Since then, there have been some attempts to recapture the proverbial magic, such as Starbreeze Studios’ attempt at remaking the game as a first-person shooter. There are also those that try to capture the appeal of the original.
Satellite Reign is one of the latter, with emphasis on “try to”.
PREMISE:
As to be expected of a game inspired by the first Syndicate, Satellite Reign has a cyberpunk setting. Corporations rule through a combination of consumerism, clandestine activities, backroom deals, monetary under-the-table incentives and of course, skullduggery. There are few attempts at resistance or revolution, due to pervasive contentment with the status quo and effective suppression.
However, those few attempts have adapted quite well – namely beating the corporations at their own game.
That game takes place in a typical cyberpunk city. The city is host to several antagonistically competitive corporations, one of whom has risen above the rest for having pioneered the technology of mind transfers. Coupled with already-established cloning and genetic engineering technology, this effectively grants the privilege of immortality to those who can afford it. Incidentally, this technology is operated through a network of satellites – hence the name of the game.
The player takes on the role of a team of operatives from a clandestine group that is purportedly aiming to dethrone the aforementioned corporation. The main goal is to supposedly introduce a viral infection into the mind transfer technology, though the expected outcome of this dastardly act is kept vague for much of the game.
That said, the player would be having the team infiltrate the holdings of the corporations, stealing things and sabotaging their apparatuses.
COMMANDOS-LIKE GAMEPLAY:
The game is described as having been inspired by the first Syndicate, and is intended to have gameplay that is similar to the first. In actuality, the game plays more like a Commandos title than (the now-defunct) Bullfrog’s game.
To elaborate, each team member is virtually a mindless goon. The only autonomy that they ever seem to express is when they come under fire from enemies. (They seek the nearest piece of cover to get behind, which is perhaps the only thing that is smart about them.) If the team members are not given at any orders, they will stay where they are and do nothing.
THE AGENTS - OVERVIEW:
The game refers to the team members as “agents”, of which there are four. Three of them are available from the get-go, whereas the fourth has to be rescued from a nearby guard station after having been captured (despite his/her specialization).
The agents are not invincible, but they are immortal; if they die, they can be spawned at the last relay beacon that they visited. (This is possible because their employer company has somehow copied the mind transfer technology for their own use.)
Thanks to their use of mind transfer and cloning technology, they can inhabit any cloned body that the player directs them to. There will be more on clones later.
Although the different agents have different innate abilities, their augmentations and equipped gear can give them overlapping capabilities. For example, only the Infiltrator can readily cloak, but the others can cloak too if they equip stealth generators.
THE SOLDIER:
The soldier is the heavy of the team. He/She has the greatest number of hitpoints (regardless of the host body) and also has abilities that increase his/her durability. The Soldier also comes with the innate ability to wield heavy weapons without any penalty, though heavy weapons would not be available until much later.
On the other hand, the gameplay is not exactly designed for sustained combat (far from it). Thus, the Soldier has to have other value in order to be relevant to actual gameplay.
This other value is the Soldier’s ability to hard-wire machines. Incidentally, as far as technology has advanced, they are still vulnerable to physical tampering; the Soldier happens to specialize in doing just that.
THE SUPPORT:
The Support is intended to keep the team alive during combat. He/She has abilities that heal and buff the team. The Support also has a skill that marks enemies, causing them to suffer more damage from hits that land.
Outside of combat, the Support’s role is to scan his/her surroundings. This scan is indiscreet and can reveal a lot of things without anyone else noticing it. Power and data lines can be traced and persons of interest can be discerned from among the mass of civilians that are milling about. Indeed, for the first-time player, the Support’s presence in mission areas would be indispensable.
THE HACKER:
No cyberpunk setting would be complete without computer science, IT or cyberspace experts. The player’s is the simply-named Hacker.
The Hacker is meant to be used on data terminals that have protection. There are no visual indicators that these terminals have them, but other agents cannot interact with these like they could unprotected terminals. A tooltip message that mentions that the Hacker is needed is also shown.
This can present a challenge in some cases. For example, prior to equipping the Hacker with a Stealth Generator, the Hacker may have to hack terminals that are being watched by security cameras or are frequented by corp-sec (corporate security) patrols.
Later, when the player gets more gear and other assets to kit out the agents with, this becomes less of an issue. For example, there is a piece of gear that lets the Hacker piggy-back the minds of his/her fellow agents, effectively allowing them to hack terminals too.
The Hacker is also the agent that can hijack other characters. In this game’s dystopian future, neural upgrades known as “mind-chips” are necessary for a person in order to maintain his/her competitiveness. However, this device also renders them vulnerable to forcible take-over of their will. There will be elaboration on hijacking later.
THE INFILTRATOR:
The infiltrator is the last team member. Indeed, the Infiltrator has – rather embarrassingly – got himself/herself caught. The team has to spring the Infiltrator out in an easy early-game mission, which shows the multiple ways of gaining entry into a restricted area.
After breaking the Infiltrator out, the cunning and wise player would quickly realize that he/she is the most valuable member of the team. This is mainly due to skills that increase his/her movement speed and abilities that provide the most efficient sneaking.
The Infiltrator also happens to be the most adept at eliminating lone targets, thanks to judicious used of a katana. (This is perhaps a reference to Shadowrun and Cyberpunk; both IPs have the katana being a rather common weapon among people of violent nature.)
MONEY:
Typically, in a game with a cyberpunk setting, money is a major resource; Satellite Reign is not an exception.
Money is needed to purchase equipment (gear, augmentations and weapons) for the agents. Money exchanges hands when the player purchases intelligence (more on this later). Money is used to make corrupt corp-sec goons look the other way.
However, money is not a long-term concern. The player may have to put it in the effort to get money for the team – namely stealing it from the corporations – but there is no limit to the cash that can be siphoned away.
THE CITY:
The cyberpunk city is composed of several districts, all of which are corporate-controlled. The player characters are practically newcomers, i.e. they initially have next to no assets on-site. Movement between the districts are also curtailed – especially to individuals that are armed. (There will be more on this movement restriction later.) Thus, the player’s endeavors for a sizable portion of the playthrough is to gain access to other districts and amass assets. Eventually, the player would reach the district that contains their main target, preferably with a lot of hardware equipped.
Heavily armed corp-sec goons patrol the streets, and there are many cameras watching too. However, complete surveillance and security coverage are not achievable, so there are many blind spots that the player can exploit. Furthermore, the regular civilians of the city are not loyal enough to report disturbances to the authorities, though they would still be alarmed if the agents do very overt things, like killing people in public.
The city and its corporate masters have assets that the player can mess with in order to gain the resources that the agents need. These will be described in later sections.
PUBLIC SPACES & CIVVIES:
Most places in the city are public spaces. The agents can move around in these places without attracting any attention. (Even though they are wearing body armor and trenchcoats with neon highlights, they are not any less eye-catching than everyone else.) That is, as long as they are not doing any alarming or suspicious things and getting spotted doing so by the authorities.

ARRESTS IN PUBLIC SPACES:
Unlike the enemies in other stealth-oriented games, enemies in Satellite Reign do not immediately outright murder law-breakers that are caught in public spaces.
The corp-sec goons on street patrols may point their guns at agents that have been accosted. If the player does not give the agents any commands, they raise their arms, signaling surrender. The goons then move to arrest them.
The arrest coincides with the application of a fine. They then escort the arrestee for a short distance. The ordeal usually ends with the goon giving the arrestee a hard kick. This is quite amusing to watch for the first time.
In actual gameplay, there are few reasons to get into such a situation, much less to take advantage of it. The player is better off not having agents caught in the first place, or just have the agents run away to somewhere secluded.
RESTRICTED AREAS:
The territories that the corporations claim as their holdings are restricted areas. Only corp-sec goons are around the buildings in these enclaves; anyone else that they discover is considered to be an intruder and is fired upon. Incidentally, most of the objective-based gameplay occurs in these places.
Interestingly, each restricted area is patrolled by the goons of whichever corporation has been assigned to its security. They will consider anyone else, including the goons of other corps, to be intruders if they find them. (If the player is expecting inter-corporate wars, the player would be disappointed; corp-on-corp violence is more of a goofy occurrence than anything else, as will be described further later.)
RESPAWNING ENEMIES:
As much as the player tries to clear an area of enemies, there will eventually be replacements that repopulate the area. This emphasizes the limitless resources that the corporations wield. How the game portrays this is not always believable though.
Most of the time, respawning enemies appear from believable avenues. For example, fresh goons may move into a cleared part of a corporate territory from other parts that have not been cleared. The player may even see street patrols moving into restricted areas that their corporations own.
However, respawning enemies can appear in secluded places that the player has already cleared and left a while ago. This is especially noticeable in restricted areas that do not have monster closets (more on these shortly).
MONSTER CLOSETS:
For better or worse, there are proverbial monster closets in the game. Monster closets are orifices or portals that fresh enemies step through, either to reinforce existing ones or replace them. In the case of this game, these are gates into peculiarly bright indoor places, from which enemies emerge.
Monster closets cannot deploy enemies all the time though. After it has spawned some enemies, it would not activate again until several minutes later, and would only do so after certain conditions have been met, e.g. goon density in the vicinity has been reduced.

DESPAWNING ENEMIES:
If the player’s team moves far away enough from a place that has enemies, the enemies eventually despawn and are replaced with others. This is useful, if the previous set of enemies are troublesome.
Enemies that have been spawned through monster closets eventually return to the closets to that they came from in order to despawn. This only happens after a quarter of an hour, however.
ALARMS:
If corp-sec goons identifies someone as a threat, one of them would eventually raise the alarm. Raised alarms cause the spawning of additional enemies, especially from monster closets.
The conditions that have an enemy trying to raise the alarm are unclear, however. One of them may raise the alarm as soon as the violence starts, or the last goon would be taking cover before attempting to raise the alarm.
CAMERAS:
Cameras in this game are typically like the cameras in stealth-oriented games. The cameras only look along small arcs, and only a segment of the arcs at any time, meaning that their pattern can be observed, predicted and avoided. If they spot anything suspicious, they will attempt to follow that suspicious person while a radial meter that represents their suspicion fills up.
After the suspicion meter fills up, another meter appears; this is the same one that is used for when enemies try to raise the alarm.
Of course, destroying cameras neutralizes them (at least until the next game-save reload; more on this later). However, this will attract the attention of nearby enemies; monster closets also activate.
FOG OF WAR:
The layout of a district is visible to the player upon having entered it for the first time. However, the people (and robots) that are traipsing about are obscured by translucent fog-of-war. The fog is uncovered as the player’s agents move about, but the fog also closes behind them.
NPCS’ LINE OF SIGHTS:
Non-player characters have visions that are very narrow, compared to those of the player’s agents. Their vision arcs are not clearly shown to the player, however.
From observation, most NPCs have an approximately 100-degree vision arc that reaches out about forty paces ahead of them. Tall obstacles obstruct their vision. They will also not spot any agents that are hiding or creeping behind low cover too. Knowing these limitations will help the player a lot in sneaking past enemies.

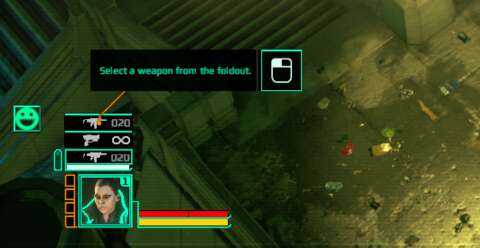
MINI-MAP:
At the top left corner of the screen, there is a mini-map. The player can stretch this mini-map and change its zoom quite readily. However, the player does not get to change the icons and colour schemes that are used. That said, it is serviceable to any player that does not have green-red colour blindness.
CITY MAP SCREEN:
In addition to the mini-map, there is the map screen that lets the player view the layout of the city in greater detail. This screen is also how the player has the entire team or individual members fast travel to relay beacons that have been deployed in the city, including across districts. This screen also shows pings for the locations of objectives, which is useful for knowing where to go next.
Like the mini-map, the colour schemes and icons of the map screen cannot be changed. There is a legend that shows the list of icons, fortunately.
CANNOT SAVE WHILE AGENTS ARE AT RISK:
When agents are placed in situations where they are at risk of being accosted or attacked, the game-saving and fast travel features are locked.
This is not new in video games of course; Black Isle’s games have this, as a form of “challenge” and a method to prevent the player from abusing save-load features for an advantage. The latter argument still has merit in the present-day, of course, but only with comprehensible reasons.
That said, this limitation is understandable if the scenarios that activate it are short. The ones in this game are not always short. There will be further elaboration on this complaint later. Suffice to say for now, the “challenge” from this limitation is not always convincing.
RELOADING GAME-SAVES RESET STATE OF GAME-WORLD:
The game cannot generate the game world to anything other than stock states. To elaborate, when a game-save is reloaded, the city is completely reverted to its default state. Any damage that the player has inflicted to corporate territories, such as the destruction of the gates that lead into them, is undone. Gameplay-wise, this is perhaps somewhat understandable, because any permanent damage would be in the player’s favour. It is not believable, however, especially if the player has been thoroughly trashing places.
Fortunately, the player’s progress in achieving objectives is retained. Yet, although there is usually no problem with this, there is the exception of missions with optional objectives about escorting a non-agent into sensitive locations.
PINGS FOR ESCORT OBJECTIVES NOT UPDATED BY GAME RELOADS:
The pings that serve as objective markers are updated according to the progress that the player has made in achieving objectives. For much of the game, this is not an issue.
However, it is an issue in missions that have optional objectives that are about escorting temporary player characters into restricted areas. To elaborate, when the objective to find this person comes out, the ping markers work as intended; there is one for the objective in the restricted area, and another for the general location of the character. If the player recruits the character, the ping for the character goes away; so far, this is understandable.
However, a problem arises if the player has made a game-save after having found the temporary character, and then reload this game-save. The character disappears, but the game considers that the character has been found and so there is no ping marker for this character’s location anymore. Fortunately, the character would return to where he/she was before he/she was recruited, but of course the player would need to remember where that was.

COVER:
Cover is significant to both stealthy and combat gameplay. Plenty of things count as cover; railings, fences, crates, containers and such. It would not take long for observant players to recognize which object counts as cover, thanks to the use of context-sensitive control inputs that are convenient most of the time. Speaking of which, icons that indicate cover-taking appear when the player brings the mouse cursor close to a viable piece of cover. These icons show the expected locations of the agents after they take cover. Shifting the cursor around changes the locations.
If there are problems with this feature, it is that the icons do not show which character would be taking which position. This is not a problem most of the time, unless the player wants them to be in exact locations. That said, the player would have to individually direct them if the player wants this.
DESTRUCTIBLE OBJECTS:
Objects that make up the boundaries of levels are impervious to any kind of damage, which is just as well because if they were not, the cunning player would be bypassing a lot of challenges. For example, the walls that ring restricted areas are indestructible, so the player cannot make a breach somewhere to sneak through.
That said, there are other things that do not have clear hitpoint meters but which can be destroyed. Typically, this is done through application of violence. However, this can be done outside of combat without alerting enemies to the agents’ presence.
To be clear, the player can have agents toss grenades at things. The explosions will raise alarms, but the grenade tosses do not reveal the location of the agents, unless they were spotted doing the deed; cloaking makes this concern moot. Alternatively, the player can have an agent plant satchel explosives, but that would mean having to deal with set-up time and not having the convenience of range.
During combat, non-explosive weapons-fire that hit cover will degrade the cover and eventually destroy it. The player is not shown the remaining durability of the piece of cover, however. There are no transitory visuals either, so the loss of cover can be sudden. Explosive attacks will destroy cover outright, by the way.
ELECTRICITY:
Quite a lot of the obstacles and hazards that the agents would come across happen to require electricity that is provided by generators. In some places, the generators are carelessly located outside of restricted areas, meaning that the player can prep for a foray into that area by dealing with the generators first. Most generators are (wisely) within restricted areas, however, and only a few are in secluded nooks that are not patrolled.
Generators can be hard-wired, causing them to be disabled semi-permanently. However, if the player’s team has left them alone for half an hour, they automatically restart. This is not told to the player in any way though, not even with a radial countdown meter.
Of course, if the player destroys the generators, they are not going to come back until the next game-save reload. Indeed, if the player is infiltrating restricted areas that are very large, it might be wise to destroy the generators beforehand.

GATES:
Gates are the most common obstacles. However, gates also impede line of sight when they are closed/raised. This can help if the player intends to sneak agents through doors when corp-sec goons open them so that they can pass through.
Most gates do not open for the player’s agents, which is understandable. However, there are side missions that can be pursued to grant permanent access through certain gates. This can reduce a lot of hassle.
Gates only open when a character is about to move through it. Close proximity does not open gates. The gates close quickly thereafter, though the player could try to time electricity cut-offs such that they are powered down while they are open. This renders them indefinitely open to everyone and will not impede line of sight.
POWERED-DOWN GATES:
Gates that were still raised when they are powered down become impassable to everyone. This can be used to hamper the movement of enemy reinforcements. Indeed, there is little that they can do, other than to mill about in front of the gate.
Some gates have secondary generators. When the gates are powered, the secondary generators can be hardwired to grant the player’s agents temporary access through the gates. This is not much of a benefit, especially if there is an alternative to gain access, e.g. the Hacker hacking a nearby control terminal.
However, when the gates are powered-down because their linked primary generator is down, these secondary generators can be used to semi-permanently raise or lower the gates. This can be used to block incoming reinforcements.
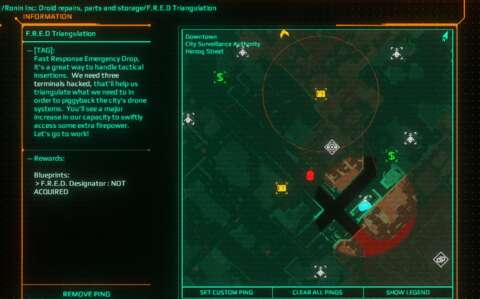
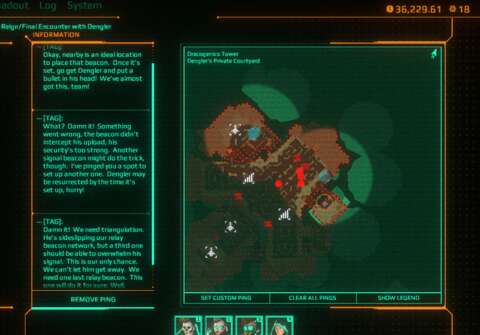
RELAY BEACONS:
The agents are being monitored and supplied via the use of compact devices – called “relay beacons” – that are communicating with compromised satellites. They seem to be invisible to everyone else.
When the agents enter a district for the first time, including the first district, there is one relay beacon that has already been deployed, often the one nearest to them at the time. It is unclear how this got there, but the tactical advisor does mention that the agents do have supporters working behind the scenes.
Anyway, this relay beacon is not enough. If the player wants to have more convenience and options for the achievement of objectives, the player needs more. For this purpose, the agent’s tactical advisor has determined locations where more relay beacons can be installed. Incidentally, these locations are often out of the way or in nooks and crannies that are obscured by tall cover. (However, they are not necessarily safe havens; this will be elaborated later.)
Relay beacons are the only means of changing the loadout of the agents. The agents must also be very close to the relay beacons for this to happen. The beacons also rapidly restore their stat meters.
As the player sets up more relay beacons within a district, mission objectives that involve the corporate territories in that district will appear.

AGENT’S ABILITIES:
As mentioned earlier, the agents have abilities that they can use to compensate for the fact that they are always outgunned and outnumbered. Ostensibly, judicious use of these would give the player the edge that is needed to beat the enemy. This is true for stealthy gameplay, but not always so for combat. There will be more elaboration on this statement later.
Some abilities are activated buffs. For example, the Soldier can go into a Rage state, which somehow increases his/her damage output. Some others are meant to be used on enemies, such as the Support’s Mark Target, which causes the targeted enemy to take more damage. Generally, there are no technical issues in learning which ability does what and when is best to use them.
SHORTCUT KEYS:
Each ability has a keyboard button that is assigned to it as a shortcut key. This is par for the course in video games. The assignment of keys even has the usual tropes, such as the same key for the same ability, if more than one agent has it due to reasons such as having the same piece of gear.
SPECIAL SHORTCUTS FOR SUPPORT’S ABILITIES:
However, there is a noticeable spark of brilliance in the implementation of the shortcut keys. The shortcut keys for two of the Support agent’s abilities can be pressed at any time, even when the agent is not selected, in order to activate those abilities. Incidentally, these two abilities – one scans the environment whereas the other slows down in-game time – are rather critical to stealth and combat gameplay respectively.
On the other hand, it is noticeable that the Support’s nano-heal ability – which affects the entire team regardless of where they are – does not have such designs for its shortcut key.
ENERGY RESERVES:
The agents have energy reserves that they tap into when they use certain abilities or when they sprint. Having a lot of energy reserves is of use to both stealth and combat gameplay. For example, Cloaking drains energy, so having higher energy reserves let agents maintain their cloaks for longer.
Energy reserves replenish automatically over time when they are not being drained. Other than being near relay beacons, there are no other means to replenish energy. Therefore, the player has to be judicious about when to expend energy.
SPRINTING:
The player can have agents sprint in order to gain a boost in movement speed, while expending energy to do so. This is of obvious usefulness in many situations.
Yet, initially, sprinting appears to be one of the most inefficient acts that agents can do. Without upgrades of energy reserves and leg augmentations that improve sprinting, the agents can only run for a laughably short distance before being exhausted.
Fortunately, there are many upgrades to energy reserves, running speed and energy efficiency while running. After receiving these upgrades, the agents can sprint for considerable distances.
POISON VENTS:
Environmental hazards are not numerous in this game. However, for some reason, there are pipelines that are leaking poisonous gases. The powers that be are described as being apathetic to these obvious hazards, so they remain ‘operational’ and are even implied to be used as deterrence against intrusion.
Anyway, all poison leaks can be manipulated by using the valves that are linked to them. In a few cases, the valves can shut off the leaks completely. In most cases though, the leaks merely change locations. Thus, this gives rise to simple (but tedious) puzzles of moving agents in tandem to the turning of the valves.
Not everyone can use the valves though, due to the torque that is needed to operate them. (This is hand-waved away as deliberate neglect of safety concerns on the part of corporate management.) Thus, this is an excuse to make the Soldier more useful than he/she seems; the Soldier is by default the agent that can turn the valves. The others can do so if they have the necessary augmentations.
MATTERS OF STEALTH - OVERVIEW:
For better or worse, the game is best played with stealthy strategies despite the inclusion of combat and really big guns.
That said, the main factor of stealth is simply staying out of sight. This is because line-of-sight is the only major concern that the player needs to be worried about; hearing and other means of perception do not matter as much, despite the sci-fi setting. Loud noises like gunfire and (especially) explosions would definitely alarm anyone who hears them, but this is not something that stealth-favoring players would cause all the time.
EFFECT OF HEIGHT:
There is actually verticality in some of the map designs, e.g. there are platforms above other platforms. The platforms do block line of sight, unless the agents are too close to the edges, in which case they can be spotted by any enemies that are looking up. Fortunately, most platforms have walled edges that obscure the agents behind them.
CREEPING AROUND:
When agents get behind low pieces of cover, they enter creeping mode. If they are directed to move behind another piece of cover (regardless of its height), the agents continue their (sometimes goofy) crouched walking. As long as there are obstacles – low or high – that are in between the agents and any onlookers, the agents cannot be spotted.
However, if the player directs the agents to go somewhere other than pieces of cover, the agents will revert to their running animations instead, thus making them more visible.

NOISE:
Noise is generally not a matter of serious concern. The agents move soundlessly, and the corporations did not equip their security forces with sophisticated sound detectors. Indeed, the player can have an agent shadow a goon closely without the fool even realizing it.
That said, noise is usually the result of application of violence, unless it has been subdued with silencers, mufflers or suppressors. Explosions can draw in many enemies from afar, though they also lure enemies away from their patrols.
CLOAKING:
Cloaking is initially only available to the Infiltrator. The other agents can eventually cloak too, if they have the appropriate piece of gear. The Infiltrator’s cloak is still the most efficient throughout the game. (That piece of gear does nothing for the Infiltrator, by the way.)
Cloaking is the player’s best tool of stealth. This is mainly because of some conveniences that make it very reliable – perhaps even overpowered.
Firstly, cloaking makes the agent invisible to anything, including even robots and cameras, at any range. Other games would impose the caveat that cloaked characters can be discovered if they are too close to enemies, but not Satellite Reign. Secondly, cloaking draws from the agent’s energy reserves – which can be upgraded. This means that cloaking gear becomes more and more useful as the playthrough progresses.
HACKING TERMINALS:
Terminals can be hacked to disable obstacles and hazards or enable shortcuts. For example, some elevators are locked on one side, but can be hacked to provide temporary access through that side.
Hacked terminals will affect anything that they are connected to. For example, restricted-access gates that are connected to red terminals will grant access to the player’s agents after those terminals have been hacked.
Hacked terminals and their connected devices do not stay compromised forever. Radial countdown meters appear over the terminals and the objects that they are connected to, thus showing the time left before the terminals and their devices reset.
That said, each specific terminal appears to have its own specific meter length and time needed to be hacked, even though it looks like the others. The most information that the player has is the level of hacking that is needed to hack the terminal, and even so this goes away after the Hacker has achieved the required level.
Still, at least the player can observe some certainties. One of these is that higher level Hacking reduces the time needed to hack a terminal and lengthens the time that it stays hacked.
DATA TERMINALS & STORY BITS:
There are data terminals with yellow lights; these yield conversation logs when hacked. For better or worse, the actual backstory and the explanation for the ending is tucked away in these.
Other than this, these data terminals are used for some side missions, usually about tracking down someone or doing someone a favor by installing software or wiping out records. They still involve the same thing though: hacking data terminals.

HIJACKING DURING STEALTH:
The Hacker can override the will of people as much as he/she can override the programming of robots. This is an unpleasant affair for the victim, so any NPC who sees this would be very much alarmed.
The Hacker cannot hide behind cover while hijacking a target. Indeed, the hijacking animation is unique, and requires the Hacker to be standing up. This makes hijacking someone in public a difficult thing to do without being caught.
Otherwise, hijacking someone or something does not appear to make a lot of noise. This is noticeably useful when sneaking through restricted areas.
HIJACKED CHARACTERS FOR STEALTH WORK:
Hijacked characters are generally not as good as the agents at matters of stealth. For one, hijacked characters will be seen as intruders if they are discovered when sneaking through restricted areas. This is so even if the characters were corp-sec goons; their former colleagues will always recognize them as being compromised. They cannot even pass through security gates. Therefore, such characters are more of a hindrance than help during stealthy gameplay.
CLONES:
Hijacked civilians happen to tie into a minor gameplay feature: clones.
As mentioned earlier, the player’s agents are not naturally-raised people; they are cunning and skilled minds inhabiting meat-puppets that have been custom-made for their dangerous work. However, the meat-puppets still require genetic material to be created, so this is where the hijacked civilians contribute. The unfortunate fools can be directed to return to somewhere to be presumably rendered down into genetic gruel.
Prior to hijacking a civilian, the player can have the Support agent scan civvies in the vicinity so that the player can look for worthwhile pedigrees. Initially, the player needs to pay some money upfront to get more details about a civilian, but the Support agent’s skill can be improved until this is not needed.
After having acquired clones that are made from hijacked civilians, the player’s agents can “equip” them, not unlike any other piece of equipment. The player should not expect a lot of sophistication here though; in addition to changing the looks of the agents, they merely impart bonuses to movement speed, health and health regeneration. There will not be any subterfuge with the cloned bodies.
That said, the player cannot have agents swap bodies willy-nilly. Any clone that is swapped into will have its bonuses diminished, purportedly because of the degradation of the genetic material. Death also causes the agent’s assigned person to degrade too, when the agent is resurrected.
ELEVATORS:
There are elevators that link two locations together. These locations are marked with the presence of distinctive doorways. Humanoid characters and small robots can move between these two locations, provided that they have access to them. (Corp-sec goons always do, by the way.)
In some cases, one or both of the doorways are access-locked. In most of these cases, the terminals that are linked to them can be hacked to temporarily remove the restriction. There are some side missions that involve tracking down the access codes for elevators that seemingly have no linked terminals; completing the missions remove their locks.
Elevators would not have been any more interesting, if not for two notable designs. Firstly, and more importantly, they act as monster closets. They do not produce as many reinforcements as the bigger monster closets, but they can surprise agents that are trying to egress through the elevators.
Secondly, elevators can be used by any human-sized enemies or smaller. Therefore, enemies can pursue agents through them. However, having agents use an elevator before enemies do almost always breaks line of sight, which is advantageous.
VENTS:
Vents work similarly to elevators, but they do not have access locks. Some vents may have poisonous gases being vented through them, which does prevent access.
Only player characters can use vents. Therefore, the player can have agents use them to egress, though of course they could encounter trouble on the other side.
Some vents are located close to the ground; any of the player’s controllable characters can use these. Some vents have their openings located high above the ground; the game calls these “high vents”. Only the infiltrator can readily use these, and only after he/she has learned the “Master Thief” skill. However, any other agent can use them too if they have the appropriate augmentations.
If the vent that characters exit from happens to be high above the ground and the characters lack the capability to use high vents, this is generally not a problem as long as the entry vent was a low vent.
FORCED USE:
By default, if an agent is not the one that can interact with something, the control input to interact with that object will not appear for that agent. However, the agent can be forced to interact with that object anyway with a specific control input.
However, there is a probability that the agent would mess up. The probability of this happening can be seen in the tool-tip that appears when the player is holding down the control input for forced interaction and hovering the mouse cursor over the object.
If the agent succeeds, the outcome is not much different from that of having the appropriate agent make the interaction. However, in the case of hacking and hard-wiring, the duration of the object being compromised is much shorter.
MISHAPS:
However, if the agent fails, a mishap occurs. Mishaps are the causes of harm and death during stealthy gameplay. For example, if any agent other than the Soldier is forced to hard-wire something and he/she fails, he/she is electrocuted. The damage is considerable.
In some cases, mishaps are guaranteed. For example, forcing an agent to use an electrified zipline is guaranteed to have the agent electrocuted. (Actually, this ‘zipline’ is a power line.) Likewise, forcing an agent to go into a vent that is having poisonous gases vented through it is guaranteed to kill the agent.
PLOT ARMOR FOR ZIPLINE MISHAPS:
Only the Infiltrator and agents with zipline gear can use ziplines without the risk of falling. Any agent that fails would fall.
Some ziplines happen to be situated over seemingly bottomless chasms, which would have meant certain death if the agent falls. However, there happen to be platforms underneath these ziplines; falling agents somehow always land on these. They take some damage, but they do not die.
Amusingly, non-agent characters – including even humanoid enemies and civilians – can use ziplines without any risk of falling. This noticeable disparity can make the agents seem inept.
USING RELAY BEACONS FOR “STEALTH”:
Relay beacons are located in out-of-the-way places. They are often surrounded by obstacles that break line of sight. Thus, they are good places for agents to run back to, if they get into trouble in public spaces.
However, the relay beacons do not appear to accelerate the dissipation of the heat that any agent has accumulated. They also do not prevent enemies from tracking agents back to the relay beacons, if the player has not been able to shake them off (which is something that should be easy to do).
SHOOTING SOMEONE IN THE BACK:
Last but not least of the stealth gameplay features, there is the means of killing an unsuspecting enemy outright. All human enemies are susceptible to this; robots and mechs are not.
If an agent can get close enough to a human enemy from behind and get his/her gun out, he/she can kill that enemy with a single shot. This can be performed with almost any weapon, perhaps excepting heavy weapons.
However, this act of murder requires the agent to aim their weapon. Aiming time is actually a statistic for any weapon; handguns take the least time, whereas sniper rifles take the longest. In the case of non-handguns, this shot also consumes ammunition.
For example, if the agent is using a sniper rifle, the aiming time is the same as for when using the sniper rifle normally. The shooting might not happen because the target has moved out of the range of the shot during that time (never mind that the target may still be in the range of a regular shot from the sniper rifle).
Thus, there is no reason to use anything other than handguns for this stealth-kill. That said, stealth kills can be gratifying if the player can set up a string of kills. For example, the player can eliminate an entire squad of enemies because they are moving in a line without anyone watching who is behind them.

MATTERS OF COMBAT - OVERVIEW:
Firstly, it should be mentioned that combat is the most poorly baked portion of the game. However, it is not an afterthought either; there is the impression that combat is intended to be a significant gameplay feature. However, poor design direction led to combat being an unreliable and inefficient way to play the game.
HITPOINTS:
Obviously, hitpoints are the indicator of a character’s durability. As long as it is not zero, the character stays alive. When it reaches zero, the character goes down; in the case of most NPCs, this is outright death.
Hitpoints are a statistic that is mostly relevant to combat. Mishaps might cause loss of health during stealth gameplay, but avoiding harm during stealthy gameplay is easier than during combat.
Hitpoints automatically replenish over time, even during combat. However, the automatic replenishment is always too slow to compensate for losses during combat, even if the player tries to upgrade the agents’ regeneration rates.
If the player wants to heal wounded agents, there are better and more immediate means. Med-packs are an option that can be equipped on any agent, for example. There is also the Support agent’s nano-healing, which is applied across any distance to every other agent.
DOWNED:
Agents that are downed do not die immediately. They can be revived before they croak; the time to do is represented with a radial countdown meter. The meter also represents the amount of time that is needed to revive them; the revival process reverses the countdown. Indeed, if another agent could reach him/her just after an agent goes down, the downed agent can be promptly revived.
That is just in theory. In actual practice, the downed agent would have been subjected to so much firepower that getting another agent to the downed one would be very unwise. Any other combat situation would not have been so dire because the player could have the agent that is under fire run away, assuming that the player had not been negligent.
The downed and revival mechanism is mostly there for the agents; NPCs die outright when their hitpoints reach zero. However, there is one enemy that does have a variant of this.
ARMOR:
The hitpoint meter is not the only thing that a character has in between staying alive and being dead. There is also armor, which has to be stripped away before hitpoints can be reduced.
Some enemies inherently have armor; almost all enemies in the end-game segments would have armor anyway. In the case of the player’s agents, armor comes from the relevant gear item that they can equip and some of their augmentations.
Interestingly, armor can regenerate, but does so slowly. Still, this will not help much during battle; any excess damage past the last point of armor overflows into hitpoints anyway.
Any agent can only have one armor-providing gear item at any time. Therefore, the player would go for the densest armor-providing gear. However, the heaviest of these also happens to impart penalties to the movement speed of their wearers, which is not desirable.
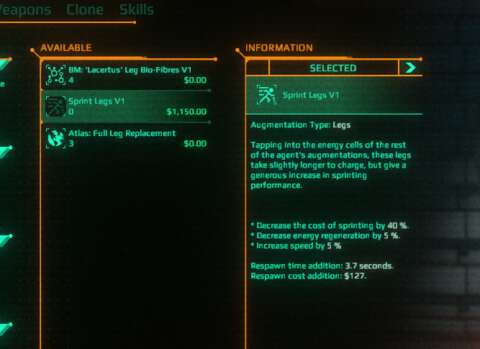
SHIELDS:
Shields are another layer of protection that can be stacked on top of armor. Where both are present, shields must be stripped away first.
Unlike hitpoints or armor, shields do not recharge all the time. Instead, a character with damaged shields must not take any fire for a while, after which shields recharge quickly. This is, of course, a game design that has been around since the first Halo title.
Like armor-providing items, shield-providing pieces of gear cannot be stacked. There are also two variants of shields; one starts recharging earlier but has lower capacity, the other is the converse.
DAMAGE TYPES:
A character with three layers of ablatives in between survival and death can be difficult to kill. Therefore, there happens to be a gameplay element that is about types of damage and how they affect these layers of protection. Incidentally, types of damage are also utilized to implement simplistic variation between different weapons.
Firstly, there is ballistic damage. Most early-game weapons inflict these, which is just as well because most characters do not have armor or shields early in the game. These weapons are most effective when used on unprotected targets. Secondly, there is laser damage. This is best used on shields. Indeed, they inflict many times more damage on shields than they do on anything else. Thirdly, there is plasma damage. This inflicts a lot of damage on armor.
In practice, it is not easy to have a variety of weapons to deal with different layers of protection. This is due to the limitation on the number of weapons that can be equipped (and poor documentation on the shortcut keys to change weapons; this will be described further later).
AMMUNITION:
The agents’ handguns have the benefit of not running out of ammo – ever. There is no in-game explanation for this, so this is very likely a gameplay contrivance. This is just as well, because handguns see the most use in both stealth and combat.
As for other weapons, they do have ammunition reserves that they draw from. Obviously, running out of ammo for these weapons render them unusable. Replenishing ammo is quite simple though; all enemies drop ammo pick-ups when they are slain, and these pick-ups are universal. There are also ammo crates that have been carelessly left unattended and unsecured; agents that mill about close to them replenish their ammo and other consumables like grenades over time.
Ammo reserves are represented as a bar and a number, next to the icons that represent the weapons in the UI. The number shows the remaining shots from the magazine/chamber of the weapon, whereas the bar shows the total amount of ammunition remaining, including that in the magazine.
HIJACKING FOR COMBAT PURPOSES:
Merely four agents may not seem enough, considering the number of goons that the corporations can throw at them. Therefore, the Hacker can be directed to hack the goons, turning some of them to the player’s side.
If the player has them scanned beforehand, the player can see what level of hacking is required to successfully hijack them. Failure to consider this requirement results in failed hijacking, and of course irate enemies.
Anyway, hacked enemies provide little more than muscle – or meatshields – for the player. They have no abilities other than fighting and can be a bother outside of combat, e.g. the player needs to keep them hidden when they are not in use. Furthermore, every enemy that is hijacked puts a strain on the Hacker’s energy reserves.
USING RELAY BEACONS FOR COMBAT:
Relay beacons are located outside of restricted areas and are in places that are not regularly patrolled. Therefore, they are very rarely scenes of intense fighting.
However, as mentioned earlier, enemies might track agents that have a lot of heat on them back to the relay beacons. The relay beacons are indestructible and will apply their rapid replenishment as long as the agents are close enough to them. Indeed, it is difficult for corp-sec goons to kill the agents if they are being energized by relay beacons. Considering that enemies rarely pass by places that have relay beacons, it should not be too difficult for the player to remove any pursuers.
ENEMIES IN BATTLE – OVERVIEW:
As mentioned already, the agents are woefully outnumbered and outgunned. In addition to soldiers packing military-grade gear, there are killer robots and mechs; the latter become more numerous later in the game. There is actually no good reason to fight them, but the player might want to see what they would do when they fight anyway.
That said, the following sections are not about their efficacy outside of combat; this is covered later in a section (that is quite scathing, so be forewarned).
STAND-UP FIGHTS ARE FUTILE:
There are no stand-up fights that lead to a good outcome. Once the alarm has been raised, enemies will keep on coming to the player characters’ last-known location. If they are still there, they will eventually be overrun, no matter how souped-up they are.
The team’s tactical advisor does mention this early on. However, the tutorial does not because the tutorial has been designed with limited enemies in mind, which might give the wrong impression to an inattentive player. That said, if the player does not realize so already, then learning the hard way would drum the lesson in.
ONLY RUNNING BATTLES ARE FEASIBLE:
If the player still wishes to go loud and somehow achieve objectives anyway, then the only option is to perform running battles.
The team have to scamper from cover to cover. If the Soldier or Hacker has to bypass something, the others have to shoot back at the pursuing mooks in order to prevent them from accumulating in numbers. Incidentally, shooting back also sometimes encourages enemies to take cover, which stall their advance.
The Support’s healing abilities will be important, if only to keep team-mates from dying; the Support’s time-slowing ability also helps here. Conveniently, there are unsecured ammo crates here and there in the enemy strongholds, so the team can attempt to restock while trying to stay mobile.
The player can also use any shortcuts that are meant for stealthy insertions too; combat does not prevent the team from using these. This can help ease the heat a lot.
Such a strategy can require a lot of hand-holding, however, due to the lack of sophisticated scripts to automate their progress through enemy territory. The benefit is much shorter time that is needed to achieve an objective, but there is of course always the risk of (temporary) death.
HUMAN ENEMIES:
Human enemies – as human as they can be, considering that many of them are cyborgs – are the most numerous. They also have the most variations; indeed, the game seems to randomize their weapons, armor and shielding.
However, they share a similarity: human enemies can be shot in the back during a fight. This can be done if the player can micromanage agents fast enough such that one agent distracts an enemy while another goes around to shoot them. However, human enemies rarely stand still, so they might avoid a shot in the back at the last second.
ROBOTS:
There are three types of robots that aid the corp-sec goons. The first and most common of these is the armed rotor drone. The rotor drone hovers in place to shoot its weapon, making it an easy target to hit. However, the drone has the best firing arcs among enemies, so expect them to land their shots more often than not, even on agents that are behind cover.
Next, there are the dog robots. These chase after their enemies and latch onto them. They do not inflict any damage, but their target is immobilized for several seconds, during which they could be shot at. The dog robots will eventually be destroyed, however.
Finally, there are the suicide drones. These have tubes of plasma jutting out of them in rather alarming ways. They skitter close to their intended targets, and will explode after a few seconds. They can be tricked into blowing up near other enemies, but this requires micromanagement on the part of the player.
MECHS:
Mechs are the most imposing enemies that the player would encounter. They are also the among the most laughable.
As their looks suggest already, Mechs are dauntingly powerful opponents. It is generally not a good idea to engage any of them; there is no in-game reward for bringing them down anyway. Indeed, if the player has not prepared for this fight, e.g. bringing heavy weapons along, Mechs would just demolish the team.
Thus, the wise player would avoid them. This is actually easier done than said, because the pathfinding scripts for Mechs are hobbled by their size and sometimes poor collision detection. The player might find Mechs that had been alerted to disturbances getting themselves trapped on a corner that they have no idea how to go around.

SENTRY TURRETS:
Perhaps the most pathetic enemy is the Sentry Turret. Of course, their debut is seemingly impressive; the first time that the player saw them, they are likely shooting at stupid civilians who strayed into restricted areas over at the checkpoints (more on these later).
In actuality though, they are lame. Firstly, they need to be powered, meaning that they cease to be a problem if the generators that are linked to them are disabled. Secondly, they have narrow arcs of vision. In fact, they are little better than cameras in this regard.
“RESEARCH” – OVERVIEW:
For what it is worth, there is a system of video-game “research” in this game too. This echoes the R&D system that was in the original Syndicate, of course.
In this game, this is described as the means to equip the agents with things that are not traceable by the corporations that control the city. It also explains why the agents could not loot guns off slain enemies (though they can extract ammo from them, as mentioned earlier).
That said, the player needs money and the schematics to make the equipment that the agents can use. Much of the gameplay will be about gathering these while having the agents gain experience and skills along the way, in preparation for the final mission against the corporation that perfected the resurrection technology.
BLUEPRINTS:
The player begins with the means to purchase only a few pieces of equipment for the agents, namely the basic ballistic guns and the silencers for them. To get more options, the player needs to find the blueprints for other equipment by stealing them from the corporations.
As for where to steal them from, they are sometimes part of the rewards from breaking into corporate buildings and escaping with the goods. The player can determine what a corporate building would yield by purchasing intel on it. (There will be more on corporate buildings and purchasing intel later.)
PROTOTYPES:
Some of the stolen stuff cannot be readily reproduced. These include the “prototypes”, which are pieces of equipment that were made prior to their mass production and implementation of security measures in the mass-produced versions. These prototypes have to be reverse-engineered in order to yield blueprints, but this requires the service of “researchers”, which will be described shortly.
The player could have agents equip prototypes anyway. However, if they go down, they drop the prototypes. If they are dropped in public spaces, they can be retrieved and returned to the player’s inventory of equipment. However, if they are dropped in restricted areas, an agent has to collect them and escape from the areas in order to return the prototypes to the player’s inventory.
Dropped prototypes do eventually disappear if they are not retrieved. If this happens, the player’s agents have to break into the corporate buildings again and commit another robbery.
RESEARCHERS:
When the Support agent scans civilians, there is a chance that a civilian is a potential researcher. If the scans discover one, there is a distinctive chime that plays. The player can then bribe this person to recruit him/her as a researcher.
Getting researchers is mostly a matter of luck. However, there are some certainties that the player can discover. For example, destitute civilians are never potential candidates.
Anyway, researchers reverse-engineer prototypes to make blueprints for them. This will destroy the prototype, so the player will want to be certain about handing over which prototypes.
RESEARCH PROJECTS:
More complex and powerful prototypes require more researchers to be reverse-engineered. The player is informed of the minimum number of researchers that is needed. These researchers have to be paid while they work on the prototype.
The player can assign more researchers than are needed in order to accelerate the project. However, there are diminishing returns here.
The player can also outsource research work if the player does not have enough available researchers for a project. This happens automatically if the project requires more researchers than there are available. Outsourcing is more expensive than using recruited researchers, however.
If the player is running out of funds, the player can choose to pause research projects in order to free up funding. However, the researchers have been committed to the project anyway and would not be freed until the project is completed.
BLACK MARKET:
If the player does not like the hassle of stealing prototypes from the corporations, the player can buy prototypes from the team’s black market contacts. They are very expensive, however, and the player can only ever purchase one unit of each prototype.
ESPIONAGE - OVERVIEW:
The following sections are for gameplay designs that have not been described earlier because they are not that easily associated with other designs. That said, these designs are what passes for corporate espionage in this game.
ATMS:
Even in this game’s cyberpunk setting, auto-teller machines (ATMs) are still around for whatever reason. No NPCs ever seem to use them. That said, the only reason for the player to take notice of them is that they can be hacked to provide the player with money over time. ATMs are often in places that are patrolled or watched over by cameras, however. Nonetheless, they are among the easiest challenges in the game.
That said, the player could just leave the game running after stashing the agents somewhere safe (typically the relay beacons), if only to accumulate money from the ATMs.
CORPORATE BUILDINGS:
Throughout most of the playthrough, the player would be getting agents into buildings in restricted areas. These buildings are often demarcated by the presence of bulkhead doors with neon markings and chevrons. The player’s agents enter the buildings through these bulkhead doors, and exit them later. There are no indoors gameplay, by the way; this can seem like a wasted opportunity.
Anyway, which agent goes into which building does matter. Usually, the mission objective that is associated with the building does mention who is most appropriate for breaking into the building.
For example, having the Soldier break into a bank would cause alarms to go off, but the Soldier can get the most money from the bank because he/she has broken into the most valuable vaults. For another example about the bank again, having the Hacker break into the bank will not trigger alarms and would only yield modest amounts of money, but the Hacker will also plant software that increases the yields from ATMs in the same district as the bank.
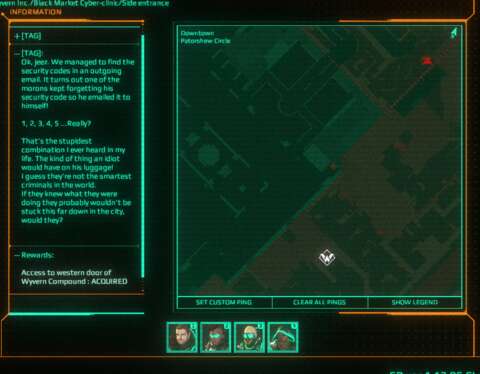
PURCHASING INTEL:
When the mission objectives involving corporate targets are revealed, there may be the option to purchase intelligence on the targets. (The intelligence is provided by an underground network that the team’s tactical advisor is in touch with, but they do not work for free.) About half of the time, they reveal the goods that can be stolen from the corporate premises, or alternative entry points into the restricted areas.
For the other half of the time though, the player would be informed about side missions that can be pursued to gain a permanent advantage in infiltrating the corporate premises. As mentioned earlier, pursuing these can give benefits when infiltrating corporate premises, like alternative entry points that are closer to the corporate buildings.
CHECKPOINTS:
The player begins in the Downtown district of the city, but the main target is in the CBD district, which is far up north with several districts in between. Entry into other districts is guarded by heavily militarized checkpoints; the corp-sec goons there simply shoot anyone who literally steps out of line. Since the player’s agents are not legal citizens, attempting to get them through these checkpoints without the proper credentials is suicidal.
Therefore, there are missions to get the necessary digital certificates to pass through the checkpoints for the first time. These missions are quite long, and often require getting into the aforementioned corporate buildings in the first place. On the other hand, the player could just fork out a lot of money to get the passes. The price for the passes does appear to lower as the player pursues and completes more of the missions.
Each checkpoint has two layers of security, by the way: one to check for travel passes, the other to check for non-civilian equipment. In the case of the latter, the bodies of the player’s agents are already loaded with non-civilian stuff in the first place; even if the player takes off all of their equipped items, they still will not get past the second scanner if they do not have the vouchsafe for their stuff.
Some districts may have more than one checkpoint connecting it to others. In such a case, the player only needs to go through one of these checkpoints to enter the other district for the first time. Afterwards, the player does not need to have the team go through the other checkpoints; fast travel between districts via the relay beacons has already been made available.
DOLES OF ISSUES - OVERVIEW:
Some complaints have been mentioned earlier, together with their associated gameplay design. The following sections are further elaborations on the complaints.
INCOMPLETE DOCUMENTATION OF CONTROL INPUTS:
Some control inputs are not documented in-game. The most notable of these omissions are the control inputs for having an agent change weapons via shortcut keys. Considering that the on-screen buttons to have agents do so are small, even when UI elements are resized, shortcut keys to do so would have been much appreciated
However, the new player would have to search the game’s forum threads to discover what these are. The developers had not thought about updates that work the documentation of these control inputs into the game.
GIMPED CAMERA:
The camera reveals its problematic limitations from the get-go.
Although the game’s engine sets it in a 3D digital world, the camera is fixed to only one facing of this world, specifically the northern hemispherical facing. This is so despite how much the player would try to manually rotate the camera, which is a sluggish process by the way. Without changing the code for the camera, the player would never see the southern facing.
Fortunately, this is not a gameplay issue, due to the simplification of the gameplay and world design that will be described shortly.
The more problematic issue with the camera is that it repeatedly drifts back and forth across a few degrees. This does not contribute to attempts at placing agents at precise locations. Fortunately, there is the option to disable this, though one would wonder why the developers thought that this is a good idea in the first place.
NOTHING WHERE THE CAMERA CANNOT SEE:
As mentioned earlier, the player would not see the southern facing of the city. This does not affect gameplay, because there is nothing important on that facing. Everything that the player needs to notice, such as the entrance to a corporate building, is in the northern facing of the city.
Of course, this is not unlike the first Syndicate game. However, that game was subjected to technological limitations at the time, e.g. the game could only use a 2D isometric engine. Satellite Reign is using a 3D engine, which gives the impression that the gameplay’s technical potential has been wasted in the attempt to limit the scope of the gameplay to an isometric view.
UNDERWHELMING AUGMENTATIONS:
For a game with cyberpunk settings and many references to cyberpunk IPs, the augmentations that the agents can have are rather disappointing.
For one, there can only be one augmentation for each body section. There had been IPs where characters can be augmented to the proverbial (and sometimes literal) gills. Considering that agents can pack more gear items than augmentations, there seem to be a mismatch between gameplay design and thematic priorities.
Moreover, although there are augmentations that allow characters to use heavy weapons or reach high vents, they cannot scale walls or drop down from higher platforms. Such actions would have emphasized the post-human capabilities of the agents and provided more options for gameplay. Ultimately, this is a wasted opportunity.
GAME-SAVE LIMITATIONS AND GAME-WORLD REVERSIONS:
Game-saving being disabled when agents are at risk has been mentioned earlier. This limitation is also put in place when the agents are infiltrating restricted areas. Some restricted areas are small, so this limitation is not a problem.
However, the other areas are expansively large, and some objectives are located deep within them. Due to the need for the agents to escape too, tackling these restricted areas can take a long time – during which unexpected things like crashes can occur.
Since the game reverts the city to its default state upon game-save loads, any progress in achieving an objective in such restricted areas could be lost due to crashes. Retracing paths is not terribly difficult, but repeating the same effort again can be wearisome, especially if there is no guarantee that there will not be another crash.
Of course, the build of the game at this time of writing is quite stable – but the abovementioned risk remains. Furthermore, even if crashes are not a concern, the fact that the game reverts the game world upon a game-save reload means that the player must dedicate play sessions to pursuing and completing objectives in their entirety.
ENEMIES ARE REALLY TERRIBLE AT PURSUIT AND SEARCHES:
As mentioned earlier, stand-up fights are futile. However, running away is laughably easy, because enemies are dumb as rocks when they are on pursuit. This can be observed after the player has agents break line of sight; their attempt at searching the last-known location of the player’s operatives are patchy at best.
Enemies are heavily reliant on their surveillance and communications network, i.e. they can only pursue the player’s agents if they stumble across other corp-sec goons or if cameras spot them (in which case the player deserves the coming hurting). Even so, they check the surrounding area where the intruders were last seen, instead of checking where the intruders were last seen going to.
Of course, bright enemies are actually a rarity – if they occur at all – in games that are supposedly stealth-oriented. Still, this means that Satellite Reign is not really raising the bar on the sophistication of enemy behavior when they search for intruders. Having played stealth-oriented games that have enemies with far better search scripts, such as Robin Hood: Legend of Sherwood, this game’s scripting is laughable.
LURING CORP-SEC GOONS INTO OTHER CORPS’ TERRITORIES:
Perhaps the most notable example of the stupidity of the corp-sec goons is that the player can lure street patrols into the territories of other corps.
The most reliable method of doing so is by blowing up the gates into restricted areas with grenades. Since the explosions are the only sources of noise in the start of this scenario, they lure both street patrols and territorial security to the gates. The street patrols will eventually and unwittingly drift into the restricted area. If they are from the same corporation, nothing happens.
If they are not, the territorial security will mark them as intruders and start shooting. The street patrol then marks their attackers as threats. This results in a street battle that can amusingly persist for quite a while, thus drawing a lot of street patrols and territorial security to the gates. It is a hilarious way to cause a distraction, but not entirely gratifying because the main cause was stupidity on the part of the enemies in this game.
LOST OPPORTUNITIES FOR INTER-CORPORATE WARFARE:
Considering that corp-on-corp battles are possible in the gameplay, there is a noticeable lack of missions that involve tricking one corps to go to war with another. Indeed, there are underpinnings in the narrative that the corporations do not like each other, and there are other nefarious organizations that do not like the corporations either. In fact, at least one of them is implied to be gearing up for war. Unfortunately, there are no opportunities to spark such wars, other than to lure stupid street patrols into restricted places.
RECYCLED OBJECTIVES:
Some mission objectives have been described earlier. However, ultimately, any convincing sophistication that they have in their designs lies in their writing. In actuality, many mission objectives have the player doing the same types of task over and over.
To elaborate, there are not many mechanically varied objectives in the missions that the player would undertake. For example, a side mission to track down the location of a person of interest and another side mission to wipe out the records of someone involve the same task: hacking yellow-lit data terminals.
Of course, one could posit that this complaint can be directed to just about any other game out there. Yet, the counter-argument is that Satellite Reign is not doing anything remarkable either. If there is anything worth complimenting (with a back-hand), it is that the writers have put some effort to distract the player from noticing that the objectives involve doing the same thing.
VISUAL DESIGNS:
As implied already, Satellite Reign is a game with mostly 2D isometric gameplay but with 3D visuals. The limited camera rotation would raise the impression that not everything in the game world has been furnished with visual details.
Nonetheless, whatever that the player can see has been lavished with details that emphasize the Blade Runner-like setting. The game is set in perpetual night, with neon lights seemingly the only illumination around. Machines are severe-looking, with little concern given to their aesthetics (other than to give them as much neon lighting as possible).
The visual designs are perhaps best appreciated via screenshots of the game though. The animations in the game have not been invested with the same effort that went into the models and textures of things in the game. Combat animations are quite impressive, e.g. human characters ducking behind cover and looking over their shoulder, but animations outside of combat are not as impressive. For example, civilians mill about, sometimes doing little more than drifting from one spot to another.
SOUND DESIGNS:
There is not a lot of legible voice-acting in the game. The only character that would be delivering full lines is “TAG”, the team’s tactical advisor. Even then, she will mention that she has to communicate via text only for most of the time in order to maintain the security of her transmissions to the team.
The only other legible voice-acting is the partially garbled radio chatter among the corp-sec goons. The chatter is of little interest, however; if the player has heard the radio chatter of security goons in other games before, these would not impress.
The sound effects that the player would hear most of the time are the noises of characters moving about. If the camera is over the player’s agents, the player can hear the soft pitter-patter of their feet (enemies will not though). Likewise, the player can hear the footsteps of enemies that are close to where the player is looking, especially if they are Mechs.
The player will also hear characters grunting when they physically exert themselves, such as when they use ziplines. These are provided by the same voice-actor and voice-actress though, regardless of the differences between the characters.
Perhaps the most interesting sounds are those of weapons-fire. Each distinct weapon appears to have been given its own audio clip. For example, plasma miniguns sound noticeably different from ballistic miniguns.
SUMMARY:
The developers of Satellite Reign appear to have expended most of their best efforts on the looks of the game. Everything else about the game – especially its gameplay – have shortfalls in their designs. These include oversights as simple as not documenting the shortcut keys to change weapons. Combat is a pointless inclusion, considering that stealthy means are far easier and more efficient at achieving objectives. The game’s attempts to present recycled objectives with different writing are also a sore point.
All these shortfalls become all the more notable if one considers the few sparks of brilliance that this game has, such as the special shortcut keys for the Support agent’s most important abilities.
To summarize this is in a brief and cynical statement, this game is a mish-mash of otherwise good ideas held by half-baked designs and packaged in neon trappings.